The Dangerous Box
As in what the NSA fears the most. Apologies for the daft name. It’s meant to be more of a description than a name. And actually there are two. They are somewhat proof of concepts, but demonstrate the achievable simplicity of an entropy source based just on a Zener diode and a single resistor. Just like our quantum entropy source on a breadboard. They are “dangerous” because they can provide anyone with a reliable, unlimited and tamper proof source of entropy for cryptography. That is potentially dangerous for authoritarianism.
Dangerous Box 1
Our dangerous little black box, based around a 24V Magnatec BZX85C24 Zener diode. Just add 30V. This is one noisy diode!

The dangerous box.
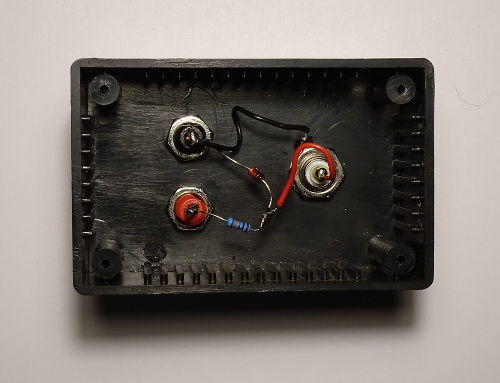
The insides, with just one diode and one resistor.
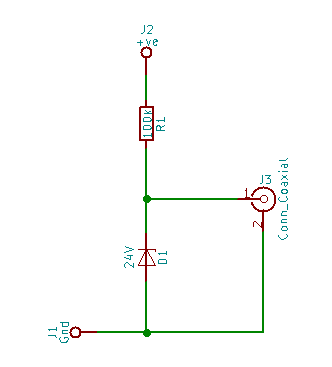
The simplest Zener entropy source schematic.
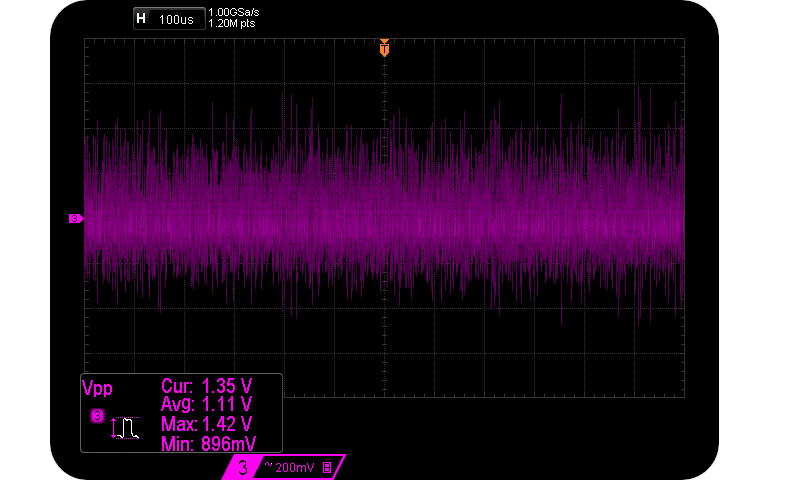
Avalanche noise from the single Zener diode.
The reasoning behind the 100us/div setting is that this will replicate a typical Arduino Uno sampling at ~10kSa/s. That’s equivalent to one sample per division. The BNC connector enables the box to be plugged directly into an oscilloscope. The noise level is at ~1.1Vpp.
Dangerous Box 2
And an other one featuring a 2N7000 MOSFET transistor voltage follower to buffer the entropy signal…

The other dangerous box.

The inside of the other dangerous box.
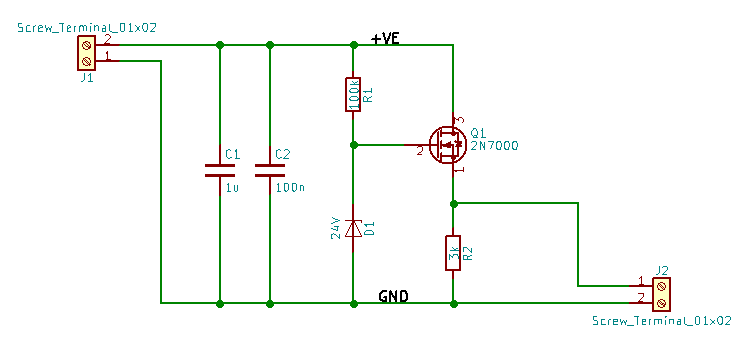
Simple Zener entropy source with MOSFET buffer.
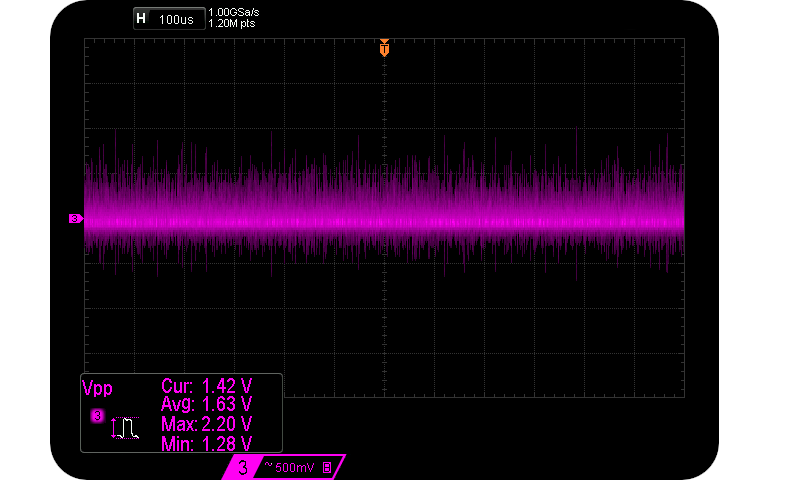
Avalanche noise from the single Zener diode with MOSFET buffer.
Notice the increased noise level, now at ~1.6Vpp. This is due partly to the stiffer output impedance, and partly due to random variations in individual diode characteristics. The capacitors (C1 and C2) simply provide some power supply bypassing.
These boxes also demonstrate the virtual impossibility of guaranteeing that a TRNG has not been subverted into producing deterministic output. Imagine if you bought a TRNG like this in a sealed black box. Perhaps it might also be epoxy resin encapsulated for tamper resistance and security. And then ultrasonically welded shut. All you’d have to check is what comes out of the BNC connector. The numbers might be uniformly and identically distributed, but there is no way to ensure they are perfectly non deterministic. Even x-raying the TRNG cannot show what is happening inside it’s potted micro controller.
You would be assembling this yourselves, but anyone could also independently validate the security of your design.